By Alexandra Zins
Throughout the related sessions at the ICANN 64 Public Meeting in Kobe, Japan, it was clear that addressing domain abuse will be a priority for ICANN moving forward. Recent news of widespread Domain Name System (DNS) attacks underscored the urgent need for registries, registrars, cybersecurity professionals, and other ICANN stakeholders to work together to prevent domain abuse and make the internet a safer place.
ICANN launched the Domain Abuse Activity Reporting (DAAR) effort in 2018 in response to a desire for consistent, neutral, repeatable reporting on domain abuse in top level domains (TLDs). The monthly report is produced using community-vetted methodology for reporting on domain registration and security threat behavior in TLD registries and registrars.
By highlighting the prevalence of domain abuse, the DAAR report also advances the importance for brand owners to employ an effective brand protection and enforcement strategy in order to mitigate against DNS security threats, thereby ensuring brand integrity online.
What is domain abuse?
Domain abuse, by common definition, refers to domains registered for phishing, malware, botnets, and spam. The existence of abusive domains threatens the DNS infrastructure, erode consumer safety, and pose a threat to critical assets for public and commercial entities.
Most commonly these methods lead to unauthorized access to information, eavesdropping on traffic, hijacking domains and/or DNS assets, IP spoofing, and denial of services (DoS) attacks. The methods used have not changed, but the ability to scale these attacks through automation and the ease of access to malicious code online has increased the volume of the attacks in recent years.
Domain abuse affects corporations directly through cybersecurity breaches and indirectly by targeting their customers with fraudulent sites. An abusive domain may be used in a phishing scheme to obtain important credentials for internal systems, but it can also be used to trick consumers with fake websites, eroding trust in the brand.
DAAR Monthly Reports
ICANN published the first set of monthly DAAR reports in February 2019, covering data from January 2018 to February 2019. These reports detail high-level trends across new and legacy TLDs and have drawn attention from contracted parties and public safety advocates. The first reports do not indicate which specific TLDs or registrars are producing the highest volume of abusive domains and the project does not intend to reveal those specifics in the future.
Key Statistics from the February 2019:
Distribution of Resolved Domains Analyzed:
- 12.2% new gTLDs
- 87.8% legacy gTLDs
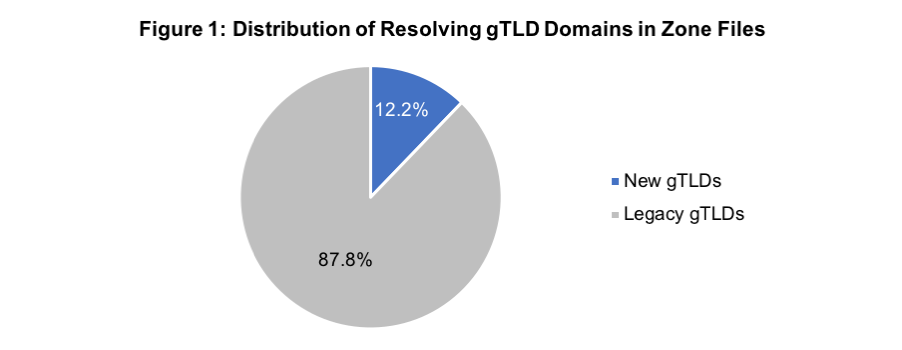
Report on data from 28 February 2019
Distribution of Abusive Domains between New and Legacy TLD Categories (Fig. 2):
- 51.4% in new gTLDs
- 13% of new gTLDs (50 out of 378) providers are responsible for 97% of the issues
- 48.6% in legacy gTLDs
- 26% of legacy gTLDs (4 out of 15) providers are responsible for 94% of the issues
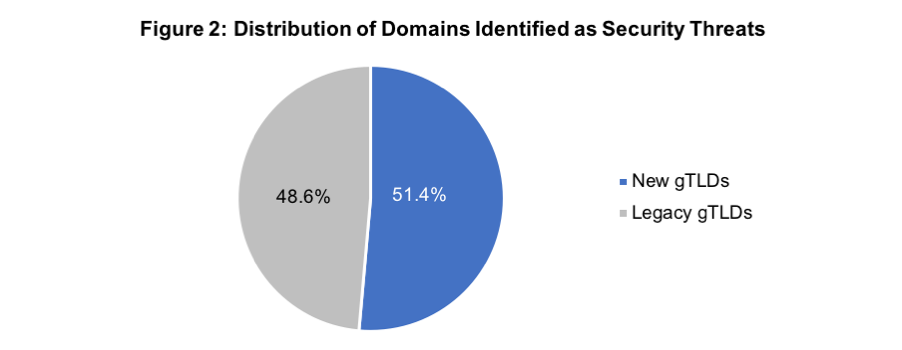
Report on data from 28 February 2019
Breakdown of Individual Security Threats (Fig. 3 & 4):
- 86.8% of identified threats were related to spam domains.
- Spam domains are more common in new gTLDs.
- Botnet C&C domains are significantly more common in legacy gTLDs
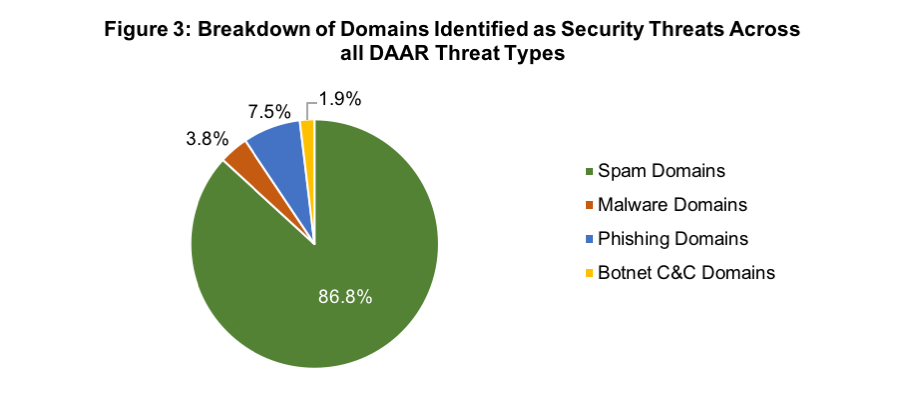
Report on data from 28 February 2019
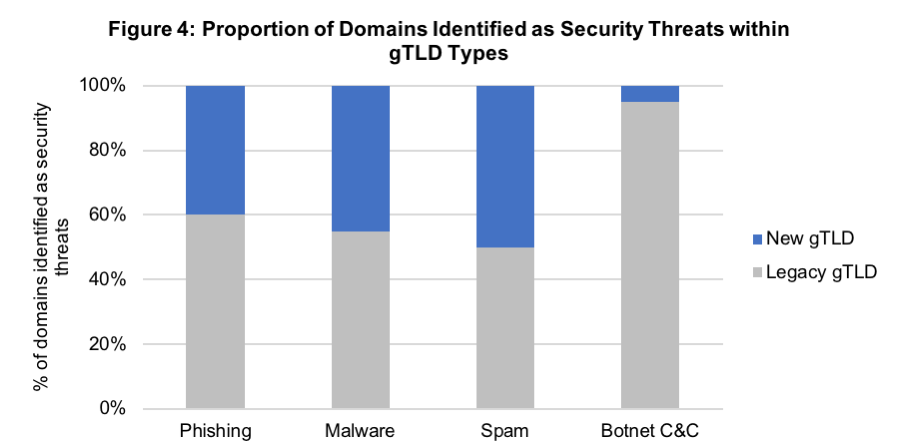
Report on data from 28 February 2019
Distribution of Abusive Domains between New and Legacy TLD Categories:
- 51.9% in new gTLDs
- within new gTLDs, less than 50 providers are responsible for 90% of the issues
- 48.1% in legacy gTLDs
- within legacy gTLDs, 4 providers are responsible for 90% of the issues
These numbers seem to indicate that domain abuse is disproportionally prevalent in new gTLDs, reaffirming the need to monitor registrations in new gTLDs. Registering trademarks in the TMCH and acting against abusive domains are some methods that mitigate a brand’s risk in the new gTLDs.
Key Takeaways
ICANN has committed resources to identify abuse in TLDs and provide this information publicly for stakeholders to use. This decision marks a notable change in ICANN’s perspective on its role in addressing domain abuse. ICANN lending its voice to this important issue paves the way for greater community collaboration when it comes to addressing abuse.
Cyber-attacks can have deep, lasting impacts on your bottom-line and brand. Domain abuse and DNS attacks are common entry points for attackers and should remain top of mind when developing a cybersecurity strategy.
ICANN urges the use of good cyber hygiene to prevent domain abuse every day. In addition, organizations can register domains that could be used in phishing schemes (i.e. typos) and take legal action against abusive domains that spread malware in their name. Incorporating defensive domain registrations, abusive domain protocols, and strong DNS security in an organization’s cybersecurity strategy makes for a more holistic approach that can reduce the risk to the brand and the critical technology infrastructure.
In order to mitigate and respond effectively against cases of DNS abuse, FairWinds offers ongoing domain monitoring services to its clients, notifying them of potential threats to their brands and trademarks online. Additionally, should our clients decide to act on our recommendations, FairWinds provides a suite of domain name recovery services, including acquiring a domain through its anonymous domain acquisition service or by taking legal action against the domain registrant.